COVID-19 changed the world rapidly and so did the corporate work environment. Companies of all sizes and segment were forced to adapt and support hundreds of thousands of employees to work remotely.
Companies were left to scramble to add more bandwidth at the data centers, call paths to keep contact centers from experiencing massive backlogs, enabling video and collaboration services to maintain employee productivity.

Behind the scenes companies constantly evaluated if their VPN architecture and security posture were designed or tested for a massive shift in employee working patterns. Many studies conducted including the ones in Wall Street Journey and Security Magazine indicate a significant number of VPN solutions were not fully designed or planned to address a large increase in their virtual workforce overnight.
Besides vulnerability to malicious activities, non-optimally architected solutions are seen to have issues with bandwidth and performance, jitter and packet loss as well as sometimes lack of reporting and end to end visibility making remote working challenging.
What corporations may need to do retroactively is engage in security audits offered by service and solutions provider focused on penetration testing and remediation scanning tools and manual techniques to identify, validate, and exploit security vulnerabilities.
Once corporations address the short term gaps in security, bandwidth assurance and reporting, tackling the siloed technology infrastructure deployed over the last two decades was not designed to support a majority of employees working remotely needs to be tackled.
Remote working needs to be integrated in business plan moving forward and not just a workplace perk or flexibility offered to a few.
Largest challenge of all that the organizations would face over the next few months and years is pivot their IT strategy to allow for a fully integrated remote working solution.
A comprehensive and cohesive strategy that holistically applies to different technology silos ranging from reliable connectivity to collaboration, zero trust identity and access management to adoption of cloud services and from end to end network monitoring to reporting, KPIs and analytics needs to be implemented. Some of the key technology areas that would allow organizations to keep employees motivated while optimizing remote worker productive are:
Build an Elastic Network
Traditional network designs using private networks to connect large corporate locations as well as remote sites to central data centers to reach to outside world and public domain are becoming history. Next generation corporate networks will need to leverage
Software based Wide Area Network (SD-WAN) to connect remote sites, utilize vendor neutral white label equipment to virtualize network functions (NFV). Centralized orchestration platform will make it possible to create and push a variety of applications to the edge and service chaining will let virtualized network functions like firewalls, routers and switches to be applied to data stream as it passes through the network. Use a mix of reliable private networks that offer QoS, economical broadband service as well as LTE/5G networks can provide differential treatment based on data type ensures reliability while controlling network costs.
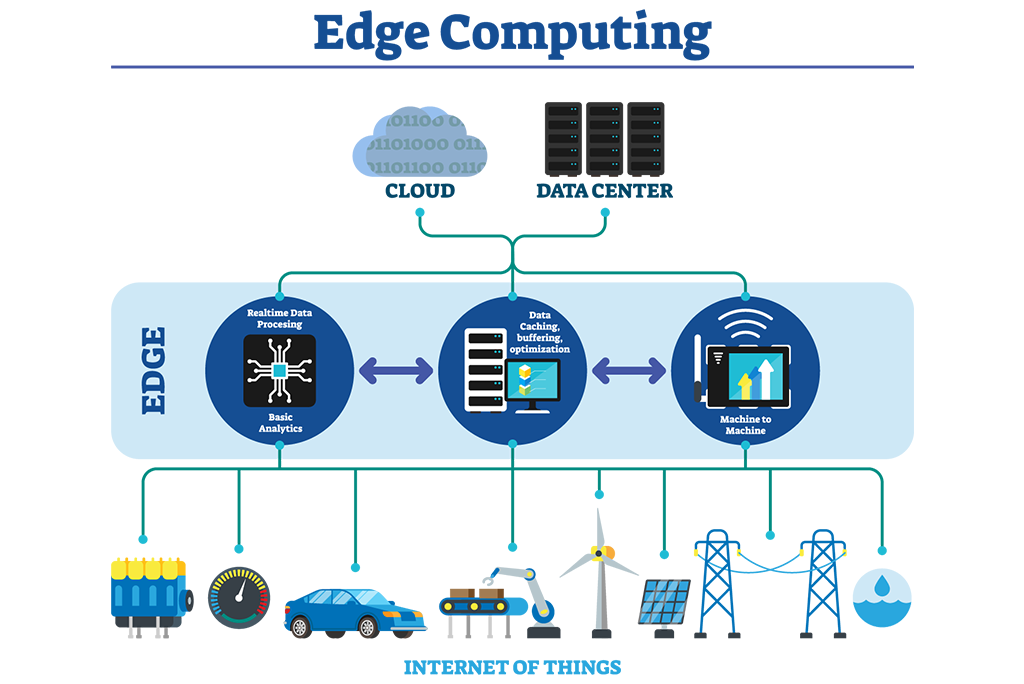
Cloud and Edge services adoption
By year 2020 most corporation use cloud applications and APIs whether for CRM, Storage, marketing, email or social media. However, the pace of cloud adoption will significantly need to accelerate to ensure enterprise database, application and communication systems that accessible within the traditional working sites now need to seamlessly cater to remote employee population.
As enterprises cruise along the path of application and data readiness for cloud migration; segmentation based on mission critical, delay sensitive vs computer and network resource intensive and the ones demanding significant storage will behoove them in a long run. This delineation will help craft the strategy in leveraging traditional cloud providers at few locations around the globe for storage and compute vs thousands of edge computing locations for lean and delay sensitive applications.
Seamless Collaboration
Analyzing the enterprise’s short and long term collaboration needs – voice, video, contact center, real time communication, APIs and automation is key along with defining modes of communication to be used internally within the enterprise vs the ones for customers, vendor, partners etc. This strategy will help identify the technology and platform to invest in to help realize the enterprise’s goal.
If your enterprise has a significant number of Contact center and customer experience agents, decoupling corporate UC strategy from the one for contact centers’ may need to be analyzed. Contact centers require an omnichannel strategy along with detailed reporting, analytics, KPI as well as threat analytics and draw traits from Artificial Intelligence to stay ahead of the competitive curve and achieve best possible customer experience.
Zero trust security architecture
Security breaches in recent years have exposed a flaw in traditional security philosophy that allowed ‘movement’ within lateral segments making it possible for hackers to navigate through the network looking for valuable assets to target. Zero trust concept is extremely critical more than ever as ‘crown jewels’ to be protected which are no longer just within the enterprise boundary or few data center locations but spread across thousands of remote home offices across the globe.
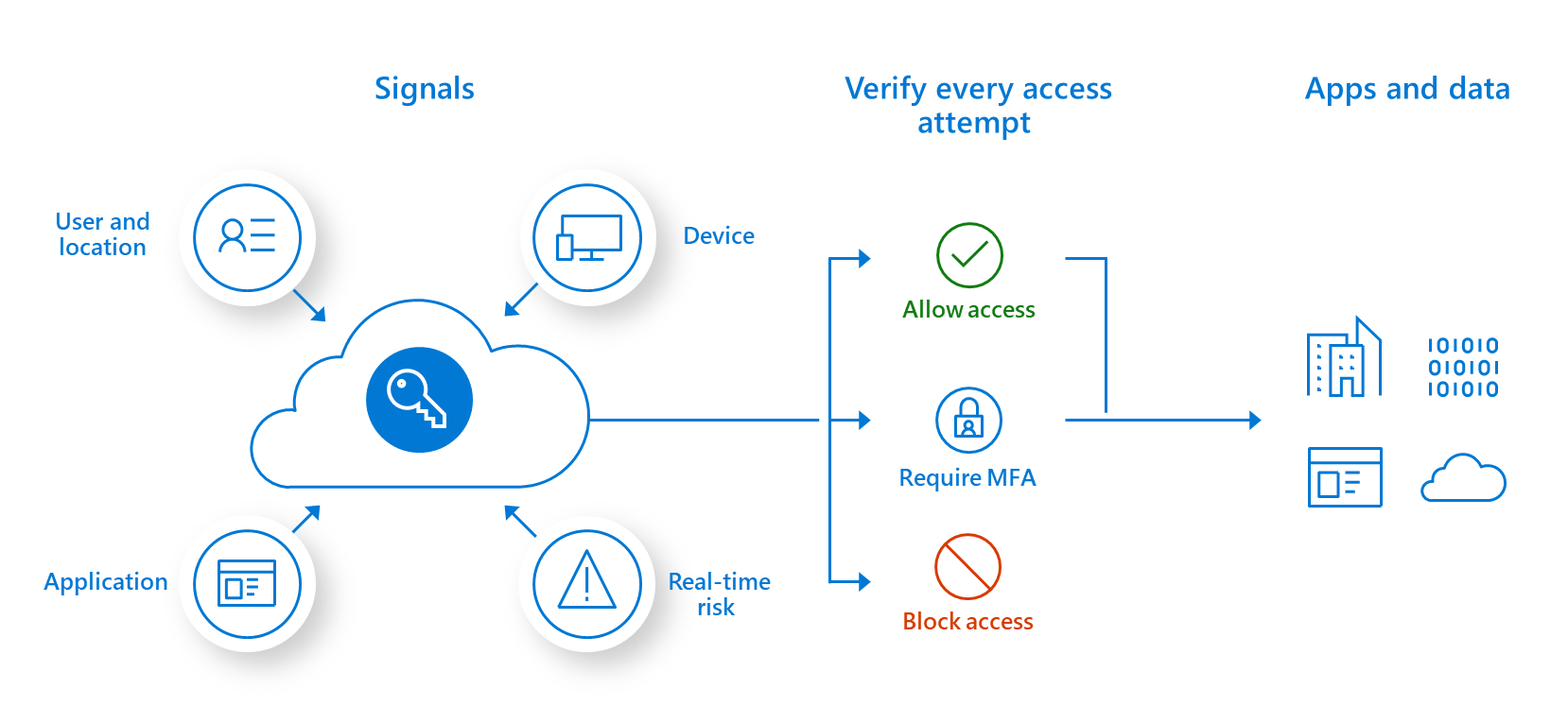
Zero trust is not about a specific product or a technology but a cradle to grave approach to securing all applications and devices. Instead of rip and replace enterprises can organically adopt zero trust architecture by combining techniques such as multifactor authentication, IAM, analytics, scoring transaction and interactions as well as encryption.
 About the Author: Bhushan Bhatt is a Sr. Solutions Architect at Verizon.
About the Author: Bhushan Bhatt is a Sr. Solutions Architect at Verizon.
In his current and previous roles, he has designed and led technology transformations across some of the largest names in the financial services industry across their Unified Communication, Customer Experience, Software Defined WAN and Security initiatives. He holds a Master degree in Computer Networking from North Carolina State University and resides in Charlotte, NC.










